Well, if you’d been waiting for DOD’s Cybersecurity Maturity Model Certification (CMMC) standards to stop being “draft” before you took a look at them, the wait is over! Version 1.0 (no longer marked draft) was released last week. DoD has indicated it will begin using CMMC requirements in requests for information starting June 2020.
Let’s take a look at some of the highlights from the recent release.
As explored in a recent post, the standards are designed to protect Controlled Unclassified Information (CUI) held by defense contractors to avoid “loss of intellectual property” and “risk to national security.” Just as before, the standards will require third-party audit of contractors and will be proportional to the size of the contractor. Interestingly, a contractor can get the certification for “its entire enterprise network or for particular segment(s) or enclave(s).”
The CMMC levels correspond to various levels of security safeguards from existing sources. As shown below, the levels incorporate increasingly more complex security practices.
- CMMC Level 1 includes all practices from FAR 52.204-21 – Basic Safeguarding of Covered Contractor Information Systems. This is a about a three page FAR clause. There are 17 required security practices.
- Level 2 is a transition between level 1 and level 3 and includes select practices from NIST Special Publication 800-171 Revision 1 (SP 800-171r1). It has 72 required security practices.
- CMMC Level 3 includes all practices from SP 800-171r1 as well as others. SP 800-171r1 is a 125-page document with “recommended security requirements for protecting the confidentiality of CUI.” It has 130 security practices.
- CMMC Levels 4 and 5 incorporate a subset of the practices from Draft NIST Special Publication 800-171B (SP 800-171B) plus others. SP 800-171B is an 81-page document that supplements NIST Special Publication 800-171 when covered “information is part of a critical program or a high value asset.” Level 4 has 156 and Level 5 has 171 security practices.
The CMMC now comes with a 338-page list of appendices with details about the requirements. Appendix B provides examples and clarifications that helpfully expand on the basic requirements.
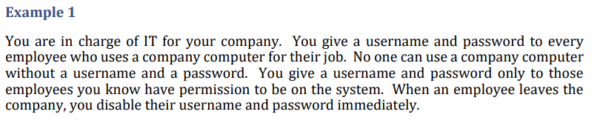
For instance, the Level 1 certification includes an access control requirement to limit access to authorized users and devices. DoD provides an example of how a company can meet this requirement:
In contrast, one of the Level 5 requirements for access control has the following example for employing a Wireless Intrusion Detection System (WIDS) to mitigate unauthorized wireless access:

There are many more examples for the various levels of certification, so be sure to take a look at the detailed guidance in this appendix.
The CMMC, then, is not reinventing the wheel. But it is putting some teeth into these standards by requiring a certification. Whereas before, contractors were allowed to self-certify, now a third-party certification is required.
The full version of the CMMC has been released. Contractors should be studying (and implementing) policies for these requirements now so that they can work towards getting the processes in place to achieve certification soon. Unfortunately, the CMMC framework does not include details about the third-party audit process. Stay tuned for more updates on these rapidly evolving requirements.
Questions about this post? Email us or give us a call at 785-200-8919.
Looking for the latest government contracting legal news? Sign up for our free monthly newsletter, and follow us on LinkedIn, Twitter and Facebook.